_
The importance of integrating MITRE ATT&CK into an NDR solution to effectively respond to cyberattacks

Cyberattacks pose an increasing threat in our increasingly connected world. Attackers employ ever more sophisticated techniques to achieve their ultimate goal. To better understand and counter these attacks, cybersecurity professionals turn to key frameworks such as MITRE ATT&CK, which allow them to gain a better understanding of the tactics, techniques, and procedures (TTP) used by cybercriminals. Integrating it into an NDR (Network Detection and Response) solution provides a significant advantage in enhancing its defense capability against cyber threats.
Let’s assess the situation together.
NDR ensures comprehensive monitoring of the computer network
The network of businesses is often considered the central nervous system of the IT infrastructure due to its crucial role in connectivity and communication among systems and devices within an organization.
An NDR solution provides a vital layer of security to this central core by detecting and responding to ongoing intrusions within the enterprise network.
Unlike traditional security solutions that rely on signature-based techniques for defense, NDR goes much further. In addition to being based on historically used Intrusion Detection Systems (IDS), it incorporates artificial intelligence, behavioral analysis, and threat intelligence to detect far beyond rule-based abnormal behaviors.
Integrating MITRE ATT&CK to maximize response to attacks
MITRE ATT&CK is a publicly accessible knowledge base that catalogs the tactics, techniques, and procedures (TTP) used by attackers. It is based on real-world attack observations.
All the information contained therein is a valuable resource for businesses and emphasizes the importance of integrating MITRE ATT&CK into a cybersecurity solution.
NDR and MITRE ATT&CK: a powerful collaboration.
L’intégrer dans une solution NDR présente de nombreux avantages pour améliorer l’investigation et la réponse aux attaques dans le réseau informatique :
- Rapid identification: Security analysts are able to quickly identify malicious behaviors and attack patterns.
- Investigation and understanding: Security teams can investigate using the provided information, gain a better understanding of potential attack methods, and respond accordingly, including leveraging the “Mitigations” section provided by MITRE.
- Compliance: Choosing a solution that integrates MITRE ATT&CK aligns with security standards, best practices, and recommendations.
- Updates: Organizations benefit from the latest threats and new attack methods through regular updates from MITRE ATT&CK. This ensures they stay up-to-date in the face of constantly evolving cyber threat landscapes.
How NDR leverages the richness of MITRE ATT&CK?
To better understand its true value, let’s outline how NDR can utilize MITRE ATT&CK:
Detection of procedures and mapping to the matrix: NDR detects various attack procedures, such as vulnerability scanning with tools like nMAP, denial-of-service tools like HULK, command-and-control channels like those used by Emotet, etc. These procedures are then contextualized based on IP addresses and temporality, and associated within the MITRE ATT&CK framework to identify attack patterns.
MITRE ATT&CK lists different tactics used by attackers that correspond to various stages of an attack, such as reconnaissance, initial compromise, privilege escalation, malware installation, etc.
It currently lists 14 tactics, and among these, NDR is the only truly competent tool for detecting the following tactics:
- Discovery
- Lateral Movement
- Collection
- Command and Control
MITRE ATT&CK also details the specific techniques used by cybercriminals to execute their tactics.
Custocy provides mapping to MITRE ATT&CK
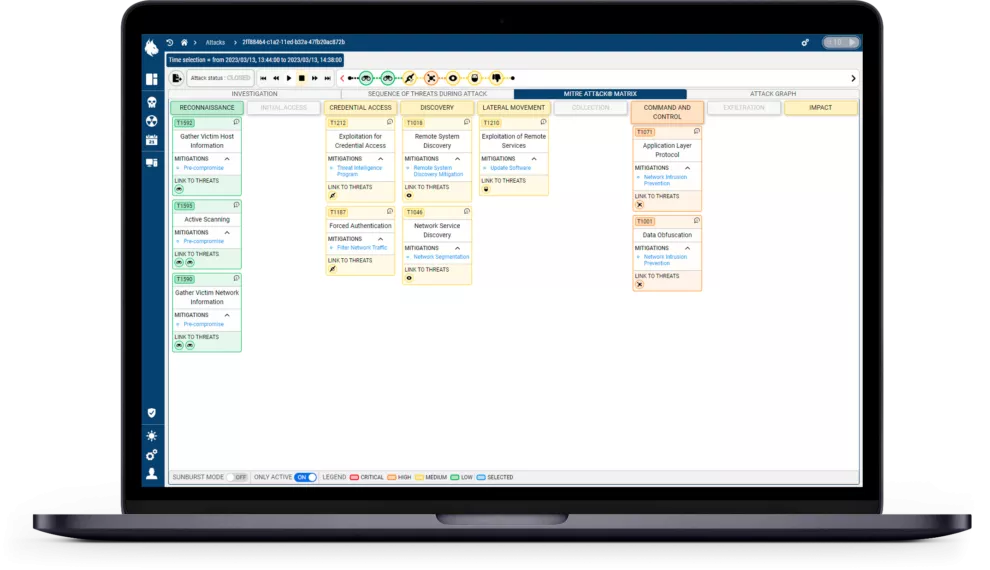
We have chosen to integrate MITRE ATT&CK into the second version of our NDR solution. Companies that adopt our solution now benefit from native integration within the Custocy interface.
Threats detected by the tool are highlighted in the MITRE ATT&CK matrix to match associated tactics, techniques, and recommended actions to mitigate them. A color-coding system (ranging from green to red) allows analysts to quickly understand the criticality of the threat at a glance.
Additionally, there is an investigation view that incorporates the “mitigations, data sources, and groups” categories from MITRE ATT&CK to provide detailed insights into the incident. This enables security teams to track each step of an intrusion and respond to incidents promptly and effectively.
In conclusion
By combining the advanced features of an NDR solution with the knowledge and information provided by MITRE ATT&CK, security teams are better equipped to proactively detect, analyze, and respond to attacks, thereby enhancing the resilience and security of their computer network.
Integrating MITRE ATT&CK is a key feature not to be overlooked when selecting a cybersecurity solution.
Curious about our NDR solution? Book your demo slot, it’s 100% free!👉HERE.
