_
We're equipped with a multitude of tools: what more can an NDR bring us?

“EDR, SIEM, Firewall: we’re already well-equipped, especially since we’re migrating to XDR!”
Such sentiments are common in the cybersecurity domain. Today, companies are equipped with a variety of tools to protect their information systems. However, this abundance of solutions can sometimes lead to confusion about their respective usefulness and the best choices to make to ensure truly robust defence.
It’s therefore crucial to take stock of this issue and understand why NDR might just be the missing piece in your security strategy.
The jungle of cybersecurity tools
Although your current tools are effective, each has its own strengths and limitations. A firewall with an IPS (Intrusion Prevention System) blocks known external threats, but it remains blind to internal attacks and those without signatures.
An IDS (Intrusion Detection System) detects suspicious activities, but it tends to overwhelm security teams with false positives and does not take automatic action.
XDR (Extended Detection and Response) integrates data from various security systems to improve visibility and threat response. However, its effectiveness heavily depends on the sources of data it incorporates.
SIEM (Security Information and Event Management) centralises security logs and events for in-depth analysis but requires intensive management.
Finally, EDR (Endpoint Detection and Response), often seen as the ultimate defence line for endpoints, also has its limits. Not all endpoints can be equipped, particularly in the case of older, incompatible devices or those restricted by company policies. Furthermore, attackers are becoming increasingly skilled, managing to bypass EDR by exploiting system vulnerabilities or using sophisticated techniques to evade detection.
NDR: a key component in the security ecosystem…
It’s in this jungle of tools that NDR (Network Detection and Response) naturally finds its place.
What sets it apart is its ability to analyse network traffic in real time, detecting abnormal behaviours and threats often overlooked by other solutions. It shines a light on the blind spots.
Unlike the perimeter protection offered by antivirus, firewalls, or EDR—which primarily monitor external access—NDR provides internal protection by analysing everything happening at the core of the network.
By using behavioural analysis techniques and machine learning (AI), NDR can identify both short-lived and long-lasting sophisticated threats, including those without known signatures. A well-designed AI in NDR drastically reduces false positives by analysing and correlating vast amounts of data to distinguish real threats from false alerts, thus simplifying the day-to-day work of security analysts.
..Which complements traditional defence tools
Although NDR is highly effective at monitoring and analysing network traffic in real time, it cannot, on its own, offer complete protection against cyber threats. Local attacks, such as privilege escalation, persistence of threats, installation of malicious tools, or attacks via USB devices, escape NDR surveillance. These are detected by EDR, specifically designed to monitor endpoints.
However, at some point, the attacker will move through the network (command & control, network discovery phases, lateral movement, data exfiltration, etc.), and that’s where NDR becomes indispensable. By analysing raw network traffic, NDR detects these stealthy movements, preventing attackers from slipping through the cracks. This is crucial because, on average, it takes just five hours for a cybercriminal to infiltrate a company’s environment and begin their operations. Without the visibility that NDR offers across the network, these lateral movements could remain invisible, rendering the defence ineffective.
SIEM complements this approach by correlating information provided by both EDR and NDR. This allows security teams to piece together the chain of events, deeply analyse the incident, and react swiftly. Together, EDR, NDR, and SIEM form a visibility triad recommended by Gartner, offering enhanced defence and a comprehensive view of suspicious activities. This synergy enables the detection, analysis, and response to incidents more effectively, strengthening the organisation’s overall security.
The innovative approach of Custocy NDR
Our NDR is built on research conducted in collaboration with the LAAS of the CNRS to incorporate AI models capable of automatically detecting threats on corporate networks.
Unlike other NDR solutions, our AI can analyse network behaviour across multiple time scales, enabling the detection of not only brief malicious exchanges but also long-term persistent attack campaigns. By combining these AI models with Threat Intelligence sources, Custocy NDR can detect various types of attacks while drastically reducing the number of false positives, allowing analysts to focus on the essentials.
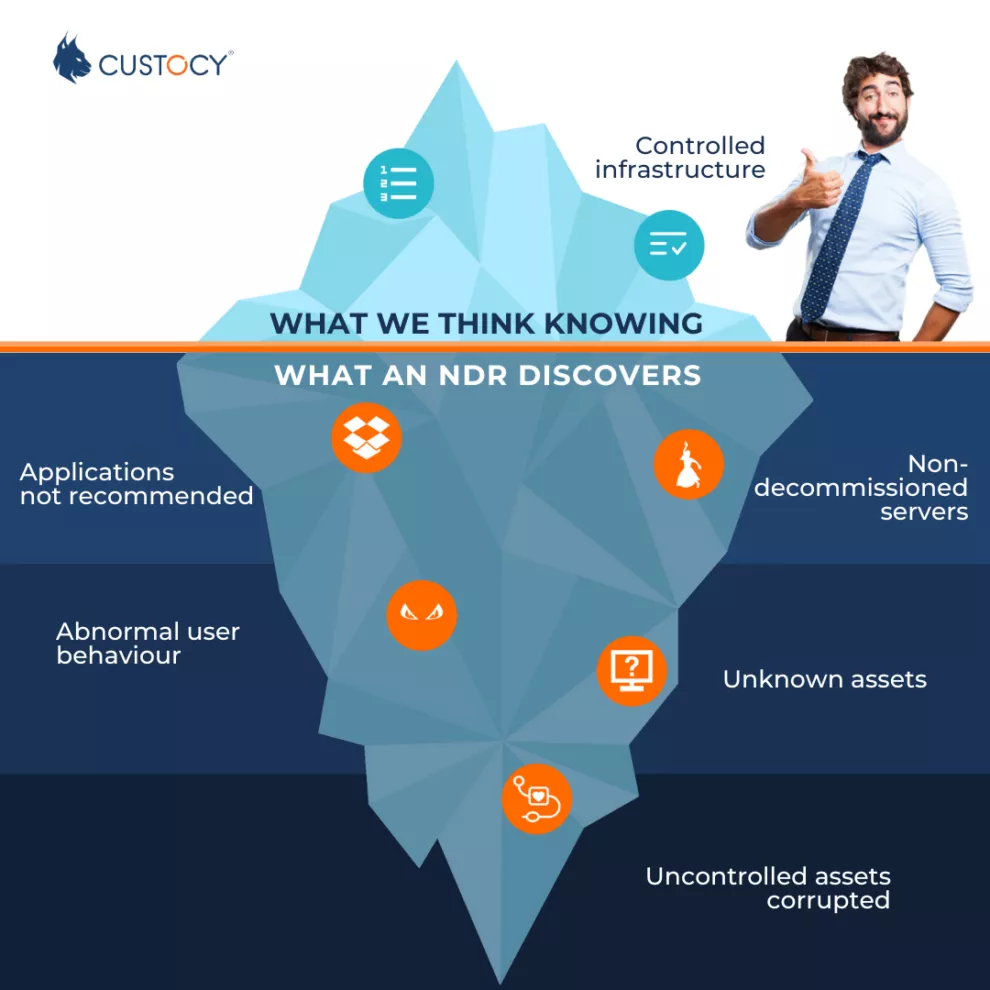
Beyond detection, our NDR also ensures good network hygiene. It’s not always easy for companies to fully manage their infrastructure. Unknown assets, unauthorised applications, vulnerabilities, shadow IT, etc., are often things that our NDR uncovers once deployed—the famous iceberg’s hidden part. Protecting against cyberattacks is, therefore, primarily about ensuring there are no vulnerabilities in your information system that can be exploited by cybercriminals.
Conclusion
Even if your current information system seems robust with traditional market tools, NDR is not just an option; it’s a necessity.
The network is the nerve centre of any IT infrastructure. In an interconnected world, it’s crucial to have complete visibility into what’s happening on it. At some point, the attacker will use the network, whether to move laterally, exfiltrate data, or compromise other systems. Without this visibility, you risk missing threats and compromising your organisation’s security. Implementing a multi-layered approach is therefore essential to ensure optimal defence, especially as threats continually evolve and attackers leverage AI as a formidable weapon to achieve their ultimate goals.
Another tool may not be one too many after all! 😉
